- Logical Networks
- Supported VLANs
- VLAN Port Membership Modes
- VLAN Configuration Files
- Normal-Range VLAN Configuration Guidelines
- Extended-Range VLAN Configuration Guidelines
- How to Configure Normal-Range VLANs
- Creating or Modifying an Ethernet VLAN
- Deleting a VLAN
- Assigning Static-Access Ports to a VLAN
- Creating an Extended-Range VLAN
Configuring VLANs
Prerequisites for VLANs
The following are prerequisites and considerations for configuring VLANs:
- Before you create VLANs, you must decide whether to use VLAN Trunking Protocol (VTP) to maintain global VLAN configuration for your network.
- If you plan to configure many VLANs on the device and to not enable routing, you can set the Switch Database Management (SDM) feature to the Distribution template, which configures system resources to support the maximum number of unicast MAC addresses.
- A VLAN should be present in the device to be able to add it to the VLAN group.
Restrictions for VLANs
The following are restrictions for VLANs:
- The number of Spanning Tree Protocol (STP) virtual ports in the per-VLAN spanning-tree (PVST) or rapid PVST mode is based on the number of trunks, multiplied by the number of active VLANs, plus the number of access ports. STP virtual ports = trunks * active VLANs on trunk + number of non-trunk ports. Consider the following examples:
- If a switch has 40 trunk ports (100 active VLANs on each trunk) and 8 access ports, the number of STP virtual ports on this switch would be: 40 * 100 + 8 = 4,008.
- If a switch has 8 trunk ports (200 active VLANs on each trunk) and 40 access ports, the number of STP virtual ports on this switch would be: 8 * 200 + 40 = 1,640
For information about the supported scalability of STP virtual ports, see the Cisco Catalyst 9500 Series Switches Data Sheet.
NoteThis applies to all Layer 3 ports, SVIs, and routed ports. This does not apply to GigabitEthernet0/0 port. Information About VLANs
The following sections provides information about VLANs:
Logical Networks
A VLAN is a switched network that is logically segmented by function, project team, or application, without regard to the physical locations of the users. VLANs have the same attributes as physical LANs, but you can group end stations even if they are not physically located on the same LAN segment. Any device port can belong to a VLAN, and unicast, broadcast, and multicast packets are forwarded and flooded only to end stations in the VLAN. Each VLAN is considered a logical network, and packets destined for stations that do not belong to the VLAN must be forwarded through a router or a device supporting fallback bridging. In a switch stack, VLANs can be formed with ports across the stack. Because a VLAN is considered a separate logical network, it contains its own bridge Management Information Base (MIB) information and can support its own implementation of spanning tree.
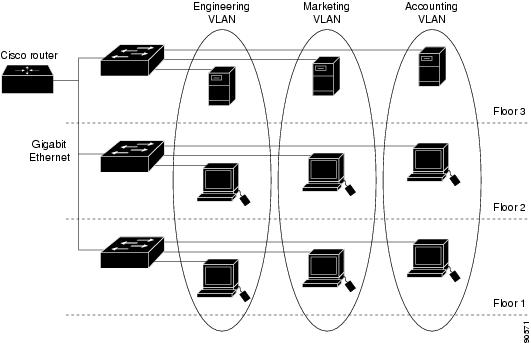
VLANs are often associated with IP subnetworks. For example, all the end stations in a particular IP subnet belong to the same VLAN. Interface VLAN membership on the device is assigned manually on an interface-by-interface basis. When you assign device interfaces to VLANs by using this method, it is known as interface-based, or static, VLAN membership.
Traffic between VLANs must be routed.
The device can route traffic between VLANs by using device virtual interfaces (SVIs). An SVI must be explicitly configured and assigned an IP address to route traffic between VLANs.
Supported VLANs
The device supports VLANs in VTP client, server, and transparent modes. VLANs are identified by a number from 1 to 4094. VLAN 1 is the default VLAN and is created during system initialization.
You can configure up to 4094 VLANs on the device. However, not all VLANs can be active simultaneously.
In the MSTP mode, you can configure 1000 active VLANs at any point in time.
VLAN IDs 1002 through 1005 are reserved for Token Ring and FDDI VLANs. All of the VLANs except 1002 to 1005 are available for user configuration.
There are 3 VTP versions: VTP version 1, version 2, and version 3. All VTP versions support both normal and extended range VLANs, but only with VTP version 3, does the device propagate extended range VLAN configuration information. When extended range VLANs are created in VTP versions 1 and 2, their configuration information is not propagated. Even the local VTP database entries on the device are not updated, but the extended range VLANs configuration information is created and stored in the running configuration file.
VLAN Port Membership Modes
You configure a port to belong to a VLAN by assigning a membership mode that specifies the kind of traffic the port carries and the number of VLANs to which it can belong.
When a port belongs to a VLAN, the device learns and manages the addresses associated with the port on a per-VLAN basis.
VLAN Membership Characteristics
A static-access port can belong to one VLAN and is manually assigned to that VLAN.
VTP is not required. If you do not want VTP to globally propagate information, set the VTP mode to transparent. To participate in VTP, there must be at least one trunk port on the device or the device stack connected to a trunk port of a second device or device stack.
Trunk (IEEE 802.1Q) :
- IEEE 802.1Q— Industry-standard trunking encapsulation.
A trunk port is a member of all VLANs by default, including extended-range VLANs, but membership can be limited by configuring the allowed-VLAN list. You can also modify the pruning-eligible list to block flooded traffic to VLANs on trunk ports that are included in the list.
VTP is recommended but not required. VTP maintains VLAN configuration consistency by managing the addition, deletion, and renaming of VLANs on a network-wide basis. VTP exchanges VLAN configuration messages with other devices over trunk links.
A voice VLAN port is an access port attached to a Cisco IP Phone, configured to use one VLAN for voice traffic and another VLAN for data traffic from a device attached to the phone.
VTP is not required; it has no effect on a voice VLAN.
VLAN Configuration Files
Configurations for VLAN IDs 1 to 1005 are written to the vlan.dat file (VLAN database), and you can display them by entering the show vlan privileged EXEC command. The vlan.dat file is stored in flash memory. If the VTP mode is transparent, they are also saved in the device running configuration file.
In a device stack, the whole stack uses the same vlan.dat file and running configuration. On some devices, the vlan.dat file is stored in flash memory on the active device.
You use the interface configuration mode to define the port membership mode and to add and remove ports from VLANs. The results of these commands are written to the running-configuration file, and you can display the file by entering the show running-config privileged EXEC command.
When you save VLAN and VTP information (including extended-range VLAN configuration information) in the startup configuration file and reboot the device, the device configuration is selected as follows:
- If the VTP mode is transparent in the startup configuration, and the VLAN database and the VTP domain name from the VLAN database matches that in the startup configuration file, the VLAN database is ignored (cleared), and the VTP and VLAN configurations in the startup configuration file are used. The VLAN database revision number remains unchanged in the VLAN database.
- If the VTP mode or domain name in the startup configuration does not match the VLAN database, the domain name and VTP mode and configuration for the VLAN IDs 1 to 1005 use the VLAN database information.
- In VTP versions 1 and 2, if VTP mode is server, the domain name and VLAN configuration for VLAN IDs 1 to 1005 use the VLAN database information. VTP version 3 also supports VLANs 1006 to 4094.
Ensure that you delete the vlan.dat file along with the configuration files before you reset the switch configuration using write erase command. This ensures that the switch reboots correctly on a reset.
Normal-Range VLAN Configuration Guidelines
Normal-range VLANs are VLANs with IDs from 1 to 1005.
Follow these guidelines when creating and modifying normal-range VLANs in your network:
- Normal-range VLANs are identified with a number between 1 and 1001. VLAN numbers 1002 through 1005 are reserved for Token Ring and FDDI VLANs.
- VLAN configurations for VLANs 1 to 1005 are always saved in the VLAN database. If the VTP mode is transparent, VTP and VLAN configurations are also saved in the device running configuration file.
- If the device is in VTP server or VTP transparent mode, you can add, modify or remove configurations for VLANs 2 to 1001 in the VLAN database. (VLAN IDs 1 and 1002 to 1005 are automatically created and cannot be removed.)
- Before you can create a VLAN, the device must be in VTP server mode or VTP transparent mode. If the device is a VTP server, you must define a VTP domain or VTP will not function.
- The device does not support Token Ring or FDDI media. The device does not forward FDDI, FDDI-Net, TrCRF, or TrBRF traffic, but it does propagate the VLAN configuration through VTP.
- A fixed number of spanning tree instances are supported on the device (See the Cisco Catalyst 9500 Series Switches Data Sheet for the latest information). If the device has more VLANs than the supported number of spanning tree instances, spanning tree is still enabled only on the supported number of VLANs and disabled on all remaining VLANs. If you have already used all available spanning-tree instances on a device, adding another VLAN anywhere in the VTP domain creates a VLAN on that device that is not running spanning-tree. If you have the default allowed list on the trunk ports of that device (which is to allow all VLANs), the new VLAN is carried on all trunk ports. Depending on the topology of the network, this could create a loop in the new VLAN that would not be broken, particularly if there are several adjacent devices that all have run out of spanning-tree instances. You can prevent this possibility by setting allowed lists on the trunk ports of devices that have used up their allocation of spanning-tree instances. If the number of VLANs on the device exceeds the number of supported spanning-tree instances, we recommend that you configure the IEEE 802.1s Multiple STP (MSTP) on your device to map multiple VLANs to a single spanning-tree instance.
Extended-Range VLAN Configuration Guidelines
Extended-range VLANs are VLANs with IDs from 1006 to 4094.
Follow these guidelines when creating extended-range VLANs:
- VLAN IDs in the extended range are not saved in the VLAN database and are not recognized by VTP unless the device is running VTP version 3.
- You cannot include extended-range VLANs in the pruning eligible range.
- For VTP version 1 or 2, you can set the VTP mode to transparent in global configuration mode. You should save this configuration to the startup configuration so that the device boots up in VTP transparent mode. Otherwise, you lose the extended-range VLAN configuration if the device resets. If you create extended-range VLANs in VTP version 3, you cannot convert to VTP version 1 or 2.
How to Configure VLANs
The following sections provide information about configuring Normal-Range VLANs and Extended-Range VLANs:
How to Configure Normal-Range VLANs
You can set these parameters when you create a new normal-range VLAN or modify an existing VLAN in the VLAN database:
- VLAN ID
- VLAN name
- VLAN type
- Ethernet
- Fiber Distributed Data Interface [FDDI]
- FDDI network entity title [NET]
- TrBRF or TrCRF
- Token Ring
- Token Ring-Net
You can cause inconsistency in the VLAN database if you attempt to manually delete the vlan.dat file. If you want to modify the VLAN configuration, follow the procedures in this section.
Creating or Modifying an Ethernet VLAN
Before you begin
With VTP version 1 and 2, if the device is in VTP transparent mode, you can assign VLAN IDs greater than 1006, but they are not added to the VLAN database.
The device supports only Ethernet interfaces. Because FDDI and Token Ring VLANs are not locally supported, you only configure FDDI and Token Ring media-specific characteristics for VTP global advertisements to other devices.
Although the device does not support Token Ring connections, a remote device with Token Ring connections could be managed from one of the supported devices. Devices running VTP Version 2 advertise information about these Token Ring VLANs:
- Token Ring TrBRF VLANs
- Token Ring TrCRF VLANs
Procedure
Example:
Device# configure terminal